Medium Access Protocol for M2M in IoT Networks
Overview
The rapid growth of both the number of connected devices and the data volume
that is expected to be associated with emerging Internet-of-Things (IoT)
applications, has increased the popularity of Machine-to-Machine (M2M) type
communication within 5G wireless communication systems. The vast number of
devices in M2M communications, their diverse service requirements, and the
unique traffic characteristics pose a real MAC layer design challenge.
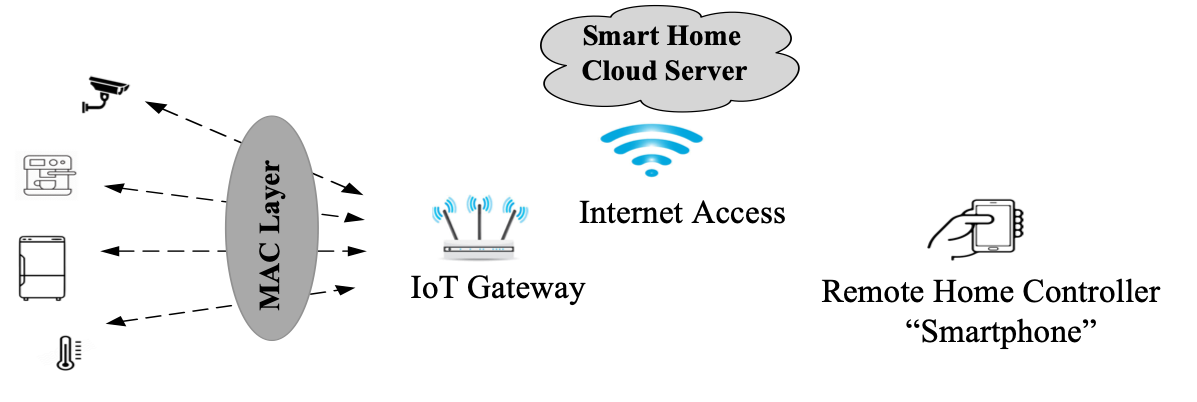
For example, in a smart home use case, the smart devices may randomly and
infrequently transmit a small burst of data to the smart home cloud server
through an IoT gateway. Uncoordinated random-access schemes have attracted
lots of attention in the standards of the cellular network as a possible MAC
protocol for making a massive number of M2M communication possible with low
signaling overhead. Because of the challenges mentioned above, I investigated,
analyzed, and implemented an uncoordinated, low-complexity MAC protocol that
guarantees access to the IoT gateway with high throughput.
I presented an enhancement to the slotted Aloha-Non-Orthogonal Multiple
Access (NOMA) protocol, where the IoT gateway adaptively learns the number
of active devices (which is not known a priori) using a form of multi-hypothesis
sting and found that the proposed Slotted Aloha-NOMA (SAN) outperformed the
state of the art CSMA/CA protocol, which is widely adopted as a MAC protocol
by many IoT technologies, in terms of throughput and average delay channel
access.
Proposed Scheme
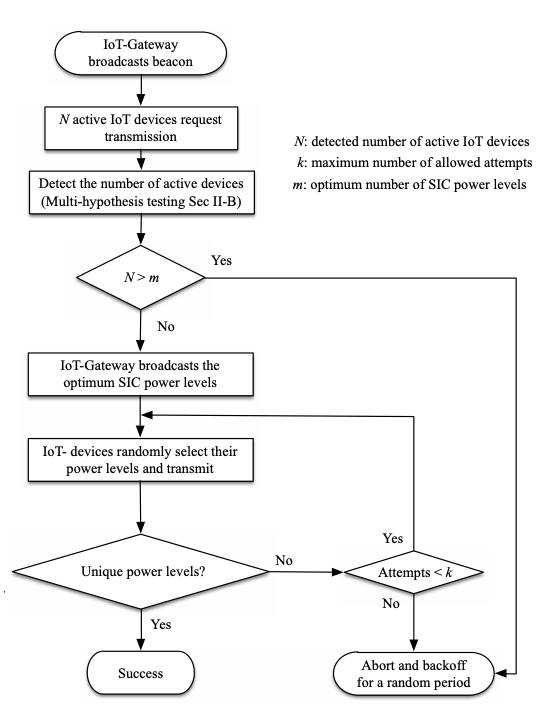
The steps of SAN protocol can be summarized as:
- The IoT gateway transmits a beacon signal to announce its readiness to receive packets.
- The IoT devices with packets ready to send a training sequence to aid the gateway in detecting the number of active IoT devices.
- The IoT gateway detects the number of devices requesting transmission using multiple hypotheses testing, which leads to two cases:
- If the detected number of active IoT devices is not in the range of the SIC capability (the number of signals that may be canceled), the IoT gateway aborts the transmission and starts the frame again by sending a new beacon signal and implying that the active transmitters use a random backoff.
- If the detected number of devices is in range, the IoT gateway broadcasts the degree of SIC to the transmitters, and then each active IoT device randomly picks one of the optimum power levels and starts the transmission.
- The IoT gateway will successfully decode the received packets (send Acknowledgment) if the IoT devices choose distinct power levels. Otherwise, a NACK will be transmitted.
For the more details please download the paper here.
