Secure Key Management for 5G Physical Layer Security
Overview
The broadcast nature of the wireless medium makes wireless transmissions vulnerable to eavesdropping.
To ensure that the information is conveyed securely, cryptographic encryption techniques are often employed in the upper layers of the communication protocol stack.
For example, symmetric cryptography methods (e.g., Advanced Encryption Standard) use a shared private key that is pre-shared between the source and destination, referred to as Alice and Bob in this paper, to encrypt/decrypt data.
In contrast to the symmetric cryptography, asymmetric cryptography methods such as Public-key Cryptosystems (PKC) use public and private keys.
In today’s mobile communication systems, symmetric cryptography has been used due to its low computational cost compared to PKC.
However, if the authorized parties do not pre-share a common key, then the key needs to be established and conveyed to both parties through a private wireless channel, that may not always exist and is prone to be intercepted by an eavesdropper, referred to as Eve hereafter.
For the next generation, wireless networks, such as 5G wireless and byond, the process of key management (key generation and secure key exchange) will become even more critical as the number of nodes increases to a massive scale, and nodes become more heterogeneous in their computational capabilities.
Also, physical layer security offers the right solution for interoperability between different systems where pre-shared keys may not exist. We envision that physical layer security methods will be used as an additional layer of security to complement traditional cryptographic methods.
Proposed Scheme
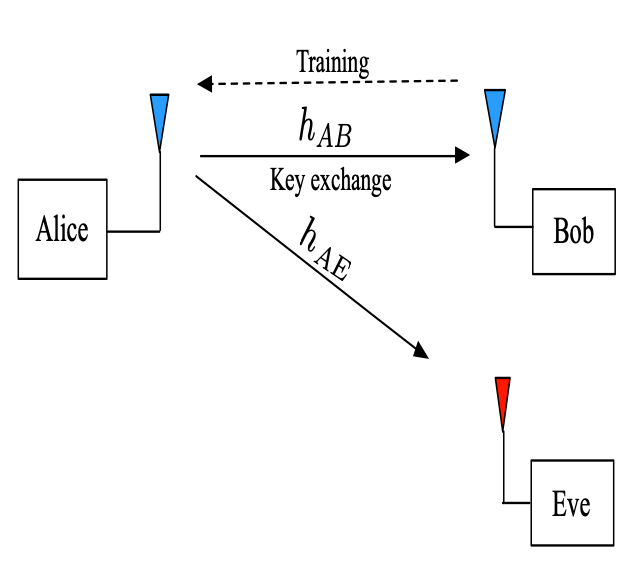
- Exploit the uniqueness of the main and eavesdropping channels.
- After Bob sends a training sequence to Alice, she computes a pre-equalization transmit filter that inverts the main channel (Alice to/from Bob).
- Alice then transmits a (pseudo-random) key over the “perfect channel” to Bob.
- Low density parity check coding (LDPC) insures a low error rate for Bob’s key reception.
- Once the secret key is established, the key is input to the random number generators (RNGs) at both parties.
- The above decreases the probability of interception at Eve.
for the more details please download the paper here.
